Once in a while question how to obscure password comes up in Support inquiries, so here is a little lean and trivial example. Not in necessary the best, but one of the ways to do it.
obscuring present participle of ob·scure (Verb)
Verb
- Keep from being seen; conceal.
- Make unclear and difficult to understand.
So it is not bullet-proof to protect your password, but only make it hard to read.
Task takes few steps:
- on Developer machine manually create file with key to encrypt/decrypt (see sample in attachments below, open with text editor)
- file with encrypted password generated on Developer machine
- two files from (1) and (2) above copied to Production machine
Let’s see Developer side first:
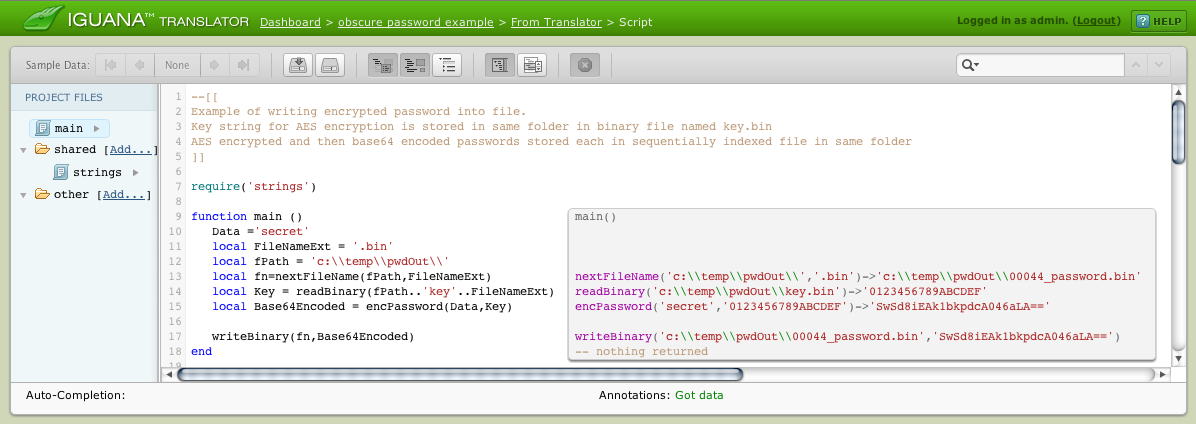
require('strings')
function main ()
Data ='secret'
local FileNameExt = '.bin'
local fPath = 'c:\\temp\\pwdOut\\'
local fn=nextFileName(fPath,FileNameExt)
local Key = readBinary(fPath..'key'..FileNameExt)
local Base64Encoded = encPassword(Data,Key)
writeBinary(fn,Base64Encoded)
end
function writeBinary(fn,binData)
local f = io.open(fn, "wb")
f:write(binData)
f:close()
end
function readBinary(fn)
local f = io.open(fn, "rb")
if (f) then
local s=f:read("*all")
f:close()
return s
end
end
function encPassword(Data,Key)
local Data = Data or 'myPassword'
local AesEncrypted = filter.aes.enc{data=Data,key=Key}
return filter.base64.enc(AesEncrypted)
end
function nextFileName(fPath,FileNameExt)
-- configure paths, etc...
local pwdFileNameSuffix = '_password'
local FilePattern = '*'..FileNameExt
local n=5 -- sets number of zeroes to pad in file name.
local nameIndex
-- if running on Win then command to use is 'dir /b'
-- on different os command will be different
local P = io.popen('dir /b '..fPath..FilePattern)
local List = P:read('*a')
for k, v in pairs (List:split('n')) do
nameIndex=k
end
-- enhance file name Index as desired ....
nameIndex=tostring(nameIndex):zfill(n)
return fPath..tostring(nameIndex)..
pwdFileNameSuffix..FileNameExt
end
After copying successfully created password and key files to Production server, we can pass password to applicable function as shown in below code snippet.
Note: The database connection in the example below has been taken as example of a password consumer. This connection is not required for password decryption itself.
--[[
Two files required to work: one with encrypted password, the other with key to decrypt.
]]
function main()
local FileNameExt = '.bin'
local fPath = 'c:temppwdOut'
local fn=fPath..'00015_password'..FileNameExt
local fk=fPath..'key'..FileNameExt
Conn = db.connect{
api=db.MY_SQL,
name='test@localhost',
user='root',
password=filter.aes.dec{
data=filter.base64.dec(
readBinary(fn)
),
key=readBinary(fk)
}
}
SQL = 'SELECT * from oSIU'
Conn:query(SQL)
end
function readBinary(fn)
local f = io.open(fn, "rb")
if (f) then
local s=f:read("*all")
f:close()
return s
end
end
Both sample projects available for download; please remember to customize paths, password, and Key values. Comments welcome.
obscure_password_example_Developer_Administrator_side.zip
